In the present situation, security is the primary concern for all Internet users. Big organizations, search engines like Google, Yahoo, Bing, and many popular websites maintain separate teams for keeping their servers secure from hackers. Not only for organizations for every internet user security is very very important.
Nowadays hackers are increasing day by day. So to keep ourselves secure from hackers we must know a lot of things of security. It ‘s hard to get knowledge about all techniques, but you must follow few crucial steps to secure your online accounts like your Email, banking accounts, credit or debit card information and other social website login details. Most of us will be having more than one Email id, but only one Email id is important for many of us.
Why should we secure our Email accounts?
Just remember those days when you were just started to use the internet at that time we all don’t know much about security. After spending some time online, few people will show their interest in security, but some people never take care of security. Let’s assume what will happen if some know your primary official email id then think what they can do?
They can change your passwords on any social media networking sites. If you are maintaining blogs, they can destroy them also. They can post some bad or any other stuff on our social media accounts. So everyone should secure their email accounts, especially it is very very important for Bloggers.
Let’s see how to secure our Email ids?
To Know, How to secure yourself from Attackers, you must know how they will try to get your passwords.
How Attackers/Hackers will try to get our passwords?
There are so many methods no one knows all the ways, but 99% of the people use fundamental techniques like phishing or sessions hijacking and remote key-loggers. If we have some basic knowledge about this, we can secure ourselves.
Tips to secure online activities
Always try to follow all of these tips to secure your online activities.
Detecting Phishing
- Many people try to hack their friends or anonymous persons account using Phishing. This is a very common method. In this technique, the attacker sends you a link and tell you something. Finally, he will ask you to log in or enter your details in that particular link. If anyone sends you a link and ask you to log in then don’t do it.
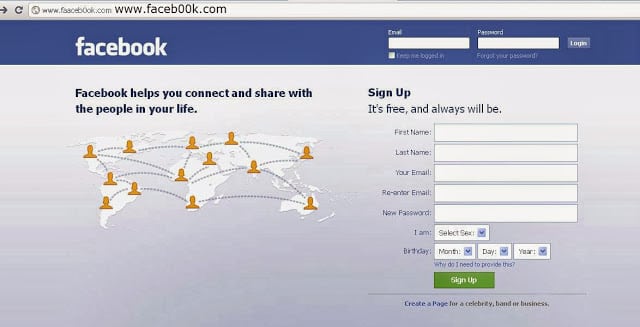
- Even if it is your close friend sends a link and tells you to log in to that page never login in that type of pages. Phishing pages look likes the below image this is an example phishing page for Facebook They look like original but you should check the URL carefully.
Using Private Browsing
Always use private browsing in browsers while using others Computer.
- To use private browsing in Mozilla Firefox, Internet Explorer use the shortcut key Ctrl+Shift+P for Google Chrome use the shortcut Ctrl+Shift+N as soon as you use these shortcuts you will see new windows of your browser always use that.
Stay Away From Public WiFi Networks
- Never use Free WiFi hotspot networks those who are providing that network can see the sensitive data if the websites don’t use proper encryption. Please don’t use WiFi network of others.
Use AntiVirus Software
- Always use a good Antivirus on your Computers and update it regularly to secure your system from remote key-loggers and from many other kinds of threats. See the Best AntiVirus for Windows 10.
Be Aware of Remote Key Loggers
- Another most commonly used method to know others passwords is Remote Key Logger method. This is a very dangerous method for victims. Remote key-loggers will send all letters that you type on your keyboard. So keep your system clean from key-loggers.
Use Two Factor Authentication
- Many majors websites are supporting Two Step verification using the mobile number to access your account. So always verify your mobile number on websites as two-step authentication. This is the best way to retrieve your password even if somebody hacks your account. Never click on remember password option when you get a prompt from browsers at the top of the page. If you select that other people who are using that computer can see that password.
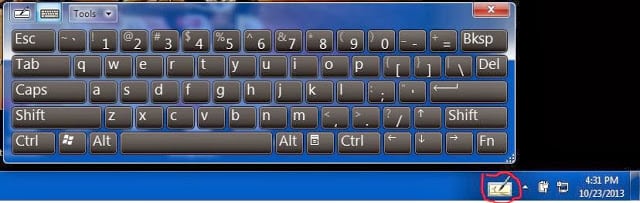
Use Virtual Keyboards
The best way is using the virtual keyboard in your system. The virtual keyboard look likes as a keyboard in our tablet or touch phones that will appear on the screen of our PC like this image. You must perform these tips to secure your Email or banking accounts.
There are so many other tips one can follow. Even I don’t know all of them, but I believe these are some of the important steps, and one should follow these always. I hope, this article is helpful.
Get all the latest security tips, subscribe and like our page on Facebook.